The Monthly Roundup: Dr Fitriani on subsea cable sabotage in the Baltic Sea
ASPI Cyber, Technology & Security Senior Analyst Dr Fitriani writes on the growing tactics of hybrid threats directed towards critical infrastructure + her top picks from the Digest this month.
This is a special edition of ASPI's Daily Cyber & Tech Digest, a newsletter that focuses on the topics we work on, including cybersecurity, critical technologies, foreign interference & disinformation. Sign up for it here.
Welcome to another edition of The Daily Cyber & Tech Digest Monthly Update! Each month, an ASPI expert will share their top news picks and provide their own take on one key story. This month, Dr Fitriani, senior analyst at ASPI CTS, shares her take.
On repeat: subsea cable sabotage in the Baltic Sea
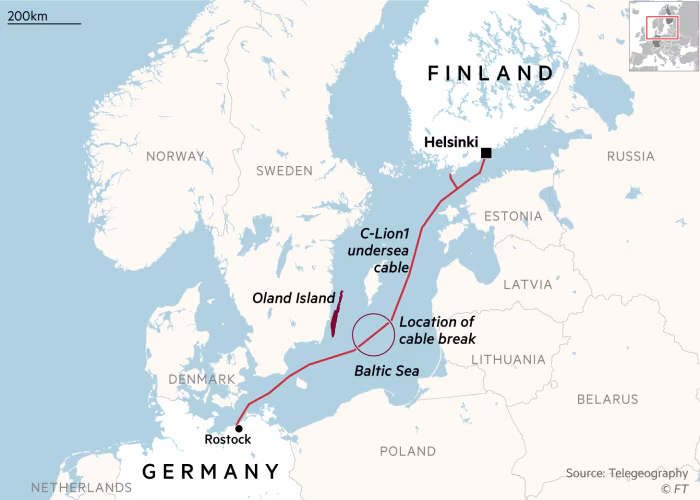
This month, two fibre-optic cables in the Baltic Sea were severed – one connecting Lithuania and Sweden, and another linking Finland to Germany – in what are perceived as deliberate acts of sabotage by a maligned actor. Authorities have ruled out technical failures, further fuelling suspicions of hostile intent. While these incidents disrupted critical data transfer, internet connectivity and national security were preserved. German Defence Minister Boris Pistorius describes the incidents as likely hybrid tactics targeting nations supporting Ukraine in its resistance against Russian aggression, as it was difficult to believe that two cables were cut coincidentally within 24 hours. As with most hybrid operations, however, the lack of clear evidence complicates attribution, hampering retribution and redress.
Source: Financial Times
Hybrid warfare strategy operates in the grey zone between peace and open military conflict, targeting and exploiting vulnerabilities in critical infrastructure, information systems and social cohesion. While accidental damage to subsea cables is not uncommon – with over 70% of incidents attributed to fishing trawlers and shipping activities – the events in the Baltic Sea suggest calculated sabotage. The region, a hotspot of geopolitical competition between Russia and NATO, has seen similar incidents before. In October last year, a subsea cable and a gas pipeline linking Finland and Estonia were severed, with Finnish authorities suspecting state actor involvement. Beijing later admitted in August this year that a Chinese vessel has caused the damage, though it dismissed the act as accidental.
The latest incident has brought the Chinese-flagged ship Yi Peng 3 under scrutiny. At the time of the incident, the vessel was sailing from a Russian port to waters between Santahamina, Finland and Rostock, Germany. Notably, NATO recently established a naval headquarter in Rostock, on which had drawn criticism from Russia. Following the incident, Yi Peng 3 was ordered to anchor by the Danish Navy to assist with investigation, on which Finland, Sweden and Lithuania partaking. It was later reported that the ship had a Russian captain and that Russia deployed a corvette to monitor the vessel. So far, US intelligence assessed that the cables were not cut deliberately, while another report indicated intentional anchor dropping and dragging.
These incidents reflect a broader trend of hybrid warfare tactics aimed at undermining the infrastructure of NATO-aligned states, while the potential involvement of China – whether as an independent actor or in coordination with Russia – signals an increasingly complex threat landscape. Though both Russia and China have categorically denied their involvement.
The international response has been weak. European countries have expressed concern over the incidents, yet none have taken punitive measures. This inaction underscores the challenges of responding to hybrid threats, where attribution remains a critical obstacle. Without definitive proof, holding perpetrators accountable becomes politically and diplomatically fraught. For example, early in May, a series of arson attacks in Europe were linked to Moscow, yet Western European nations responded only by raising alert levels. Such limited responses risk emboldening adversaries.
To counter these hybrid threats effectively, NATO and its allies must adopt a more robust and proactive approach. While the establishment of the Maritime Centre for the Security of Critical Undersea Infrastructure earlier this year was a positive step, it remains insufficient to address the scale and sophistication of the challenge. Stronger deterrence measures are urgently needed.
A recent report by ASPI underscores several key recommendations for strengthen subsea cables resilience. These include bolstering the capability to maintain and repair, as well as enhancing active monitoring of the cable infrastructure.
It is also important to improve attribution capabilities by investing in technologies and intelligence-sharing frameworks. Additionally, countries need to develop legal and policy frameworks that action punitive measures on perpetrators, such as targeted sanctions and restrictions on vessels implicated in acts of sabotage.
My must-reads
How Russia openly escalated its election interference efforts (The New York Times)
The Kremlin’s information warriors not only produced a late wave of fabricated videos that targeted the electoral process but also no longer bothered to hide their role in producing them, unlike what it did in the past. The action was so blatant that the US agency ODNI, FBI, and CISA issued a joint statement on the matter.
Top Chinese research institutions linked to the PLA have used Meta's publicly available Llama model to develop an AI tool for potential military applications. The researchers used an earlier Llama 13B large language model, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
Australia Annual Cyber Threat Report 2023-2024 (Australian Signals Directorate)
The Australian Signals Directorate has released its annual cyber threat report, and while some numbers show an overall improvement in the threat landscape, others show new cyber-crime trends impacting the country’s population and organisations. Australia’s cyber security hotline received nearly 37,000 calls in the 2023-24 financial year — up 12%. The average self-reported cost of cybercrime for impacted individuals also jumped 17% to $30,700.